5 important topics of 7 layer OSI model by Kenno
An attempt to fundamentally understand a universal communication standard.
This article is written by Kenno 🐛 and I’m just a middleman publishing it under my account. Why? Maybe it's because I’m under a spell or hypnotized by something … who knows? 😞
1. WHY ?
Why can I use a Dell mouse with a Lenovo computer? Why can Apple, HP, Acer, and computers from different vendors connect to the same network broadcasted by a Linksys router? 🤔
These silly questions are no longer asked. The majority of the software and technology we use every day today is platform agnostic. As a user, we don't have to be concerned about an app's cross platform compatibility because a compatible version of the app is already available for the platform we use. With few or no exceptions, all computer devices and programs should be able to communicate with one another as necessary, regardless of their manufacturer. This is quite normal today but It's worth noting, though, that this was not always the case.
When "Computer Networks" were initially introduced, computers could only communicate with other computers made by the same manufacturer. For example, ARPANET could only use BBN-IMPs, and organizations could only implement either a complete DECnet solution or an IBM solution, never both together, because different vendors developed products and services using their proprietary communication standards. As you may guess, this incompatibility among manufacturers was a significant impediment to progress and promoted monopoly. To ensure interoperability and maintain fairness in this arena, a universal communication standard was required and the Open Systems Interconnection model was born.
2. WHAT is the OSI model?
The Open Systems Interconnection model (OSI model) is a conceptual model that describes the universal standard of communication functions of a telecommunication system or computing system, without any regard to the system's underlying internal technology and specific protocol suites. ~ Wikipedia
A model which was developed by ISO to interconnect devices from different vendors and successfully communicate with them, which is open to all or accessible by everyone. We can think of this model as a blueprint of computer networking.
3. History
Charles Bachman, an American computer scientist at Honeywell Information Systems, developed the concept of a seven-layer model. Collectively the experiences with the NPL network, ARPANET, CYCLADES, European Informatics Network, and the International Networking Working Group influenced several elements of OSI design (IFIPWG6.1) like splitting the functionality into layers of different protocols.
The initial development of the OSI model started in the late 1970s to facilitate the emergence of the diverse computer networking methods and Hubert Zimmermann, a French software engineer defined the first OSI model in raw form in Washington, DC in February 1978, and the ISO released the refined but still draft standard in 1980.
Engineers, corporations, and governments were divided from the 1970s to the 1990s over which communication protocol would result in the greatest and most reliable computer networks. The Protocol Wars ⚔️were a long-running discussion in computer science that was eventually won by TCP/IP.
4. Then why should we bother about the OSI model?
Well, first and foremost, since understanding the OSI model will help us comprehend TCP/IP in a better way, which I'll be covering in a later post, and also it will assist developers and manufacturers understand the concepts at work behind the scenes of a platform neutral product.
Hopefully, you're still fascinated about the OSI model 💪🤩and as eager as I am to learn how data flows from a sender to a receiver and how each layer treats it along the way. I must admit that this is not an in-depth article on the OSI reference model. To paint 🖌️a basic picture🖼️ of the model, I took the risk of omitting some details that I considered were unnecessary and have attempted to present the subject matter in basic terms so that the workings of a worldwide communication standard can be easily visualized.
5. How does a universal communication standard work?
We'll start by looking at the image below and pausing for a moment before attempting to decipher how data is processed and transported from source to destination layer by layer.
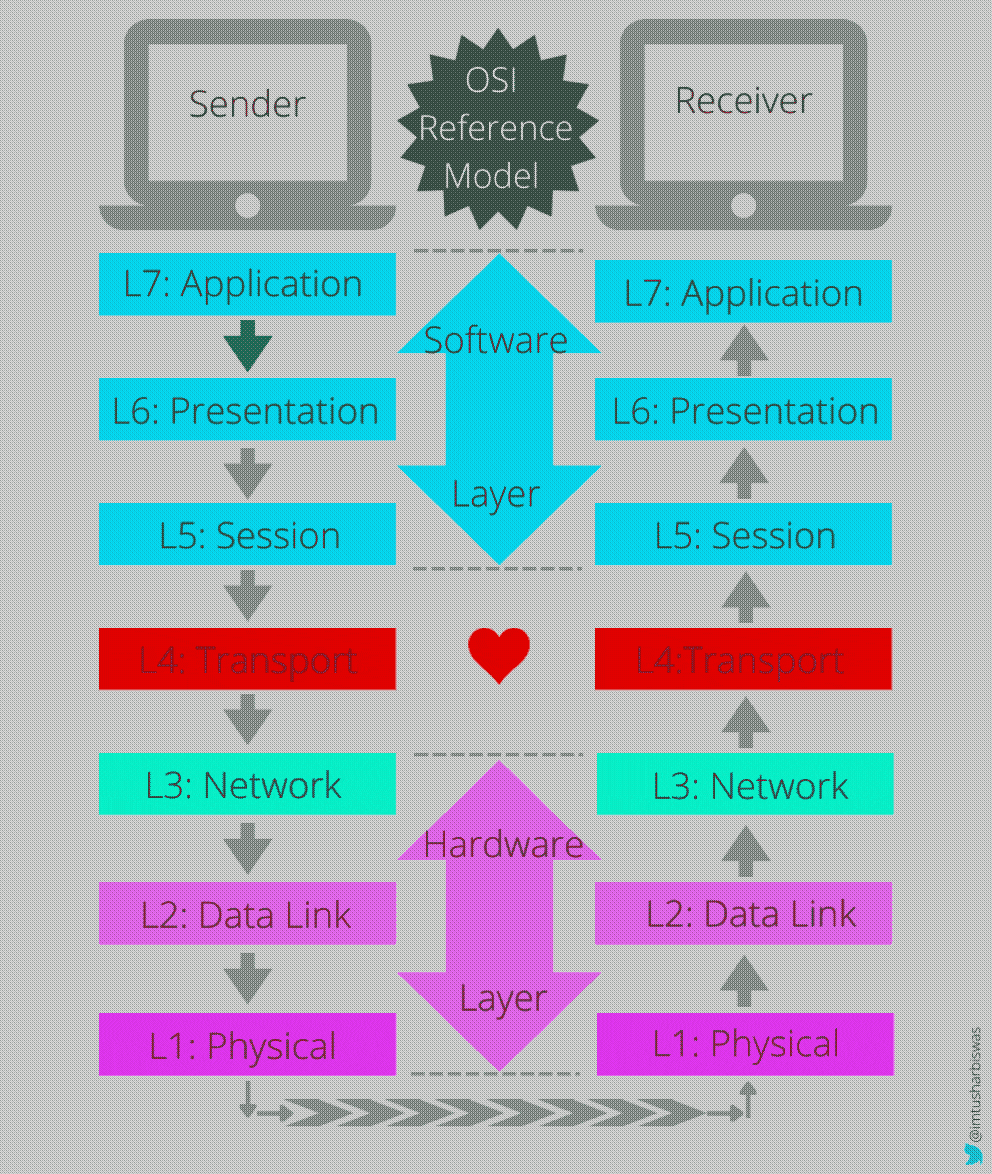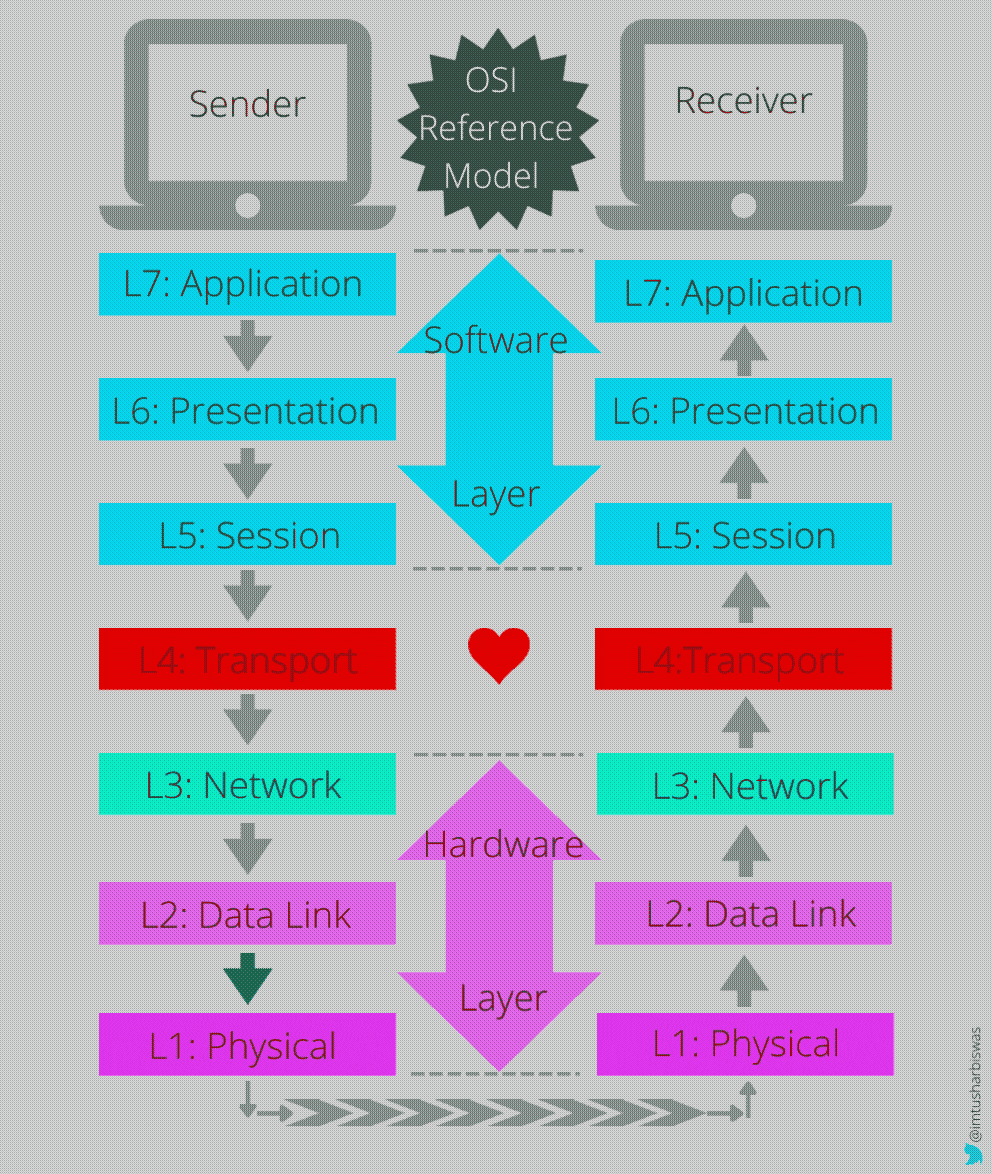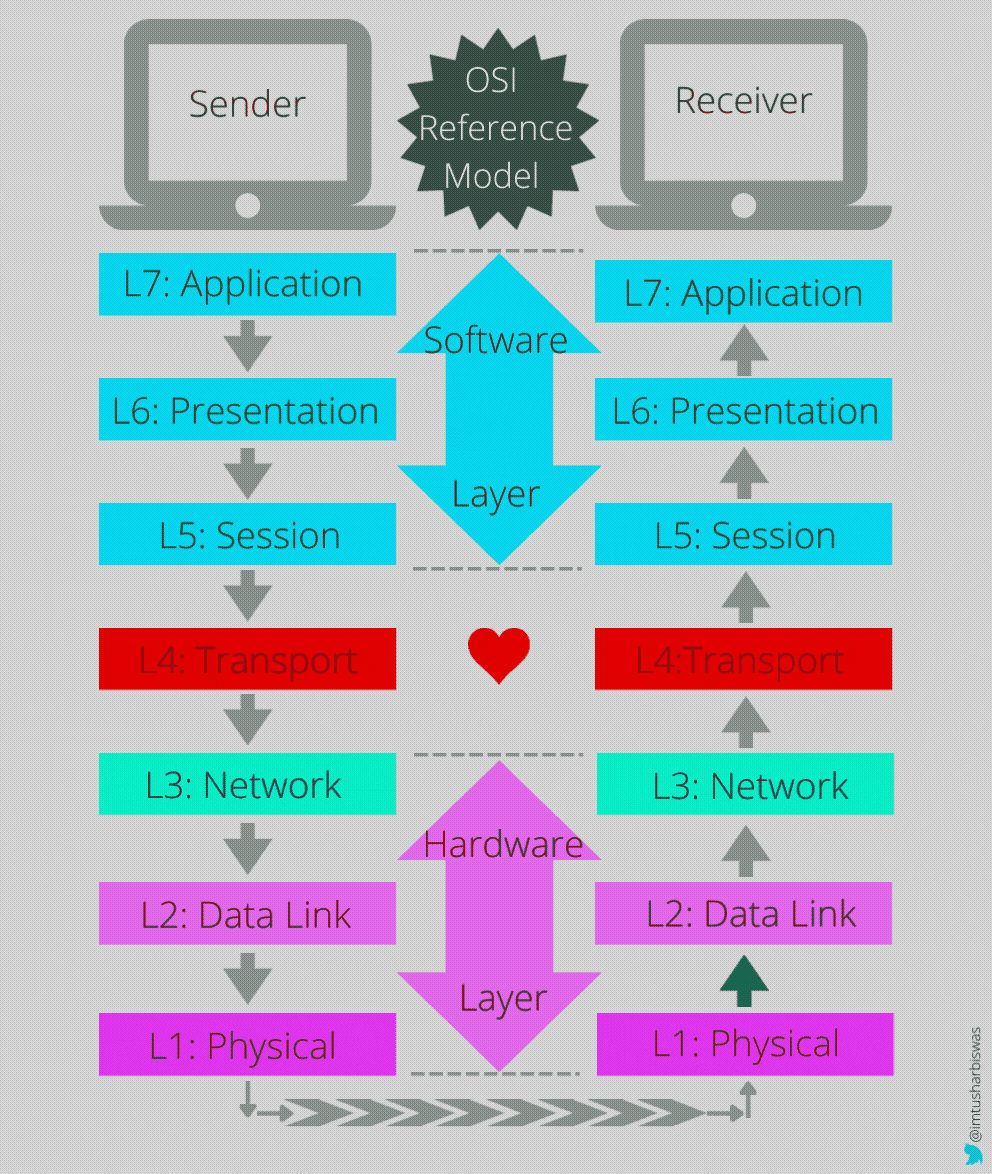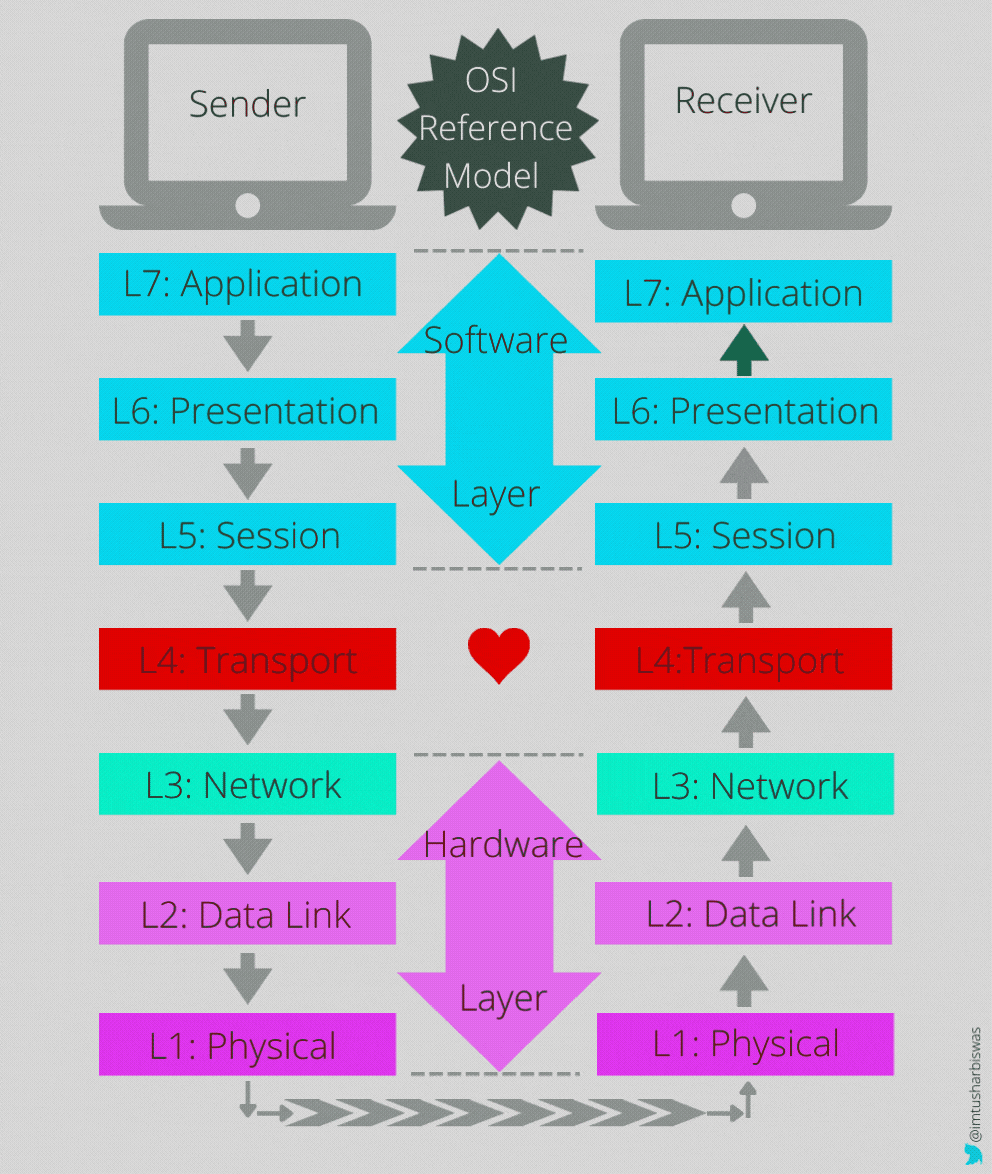
Application Layer-7
An application layer is an abstraction layer that specifies the shared communications protocols and interface methods used by hosts in a communications network. An application layer abstraction is specified in both the Internet Protocol Suite (TCP/IP) and the OSI model. Although both models use the same term for their respective highest-level layer, the detailed definitions and purposes are different. ~Wikipedia
It is the OSI model layer nearest to the end user and the initial point of interaction. A collection of application layer protocols makes up our application layer. HTTP, FTP, SMTP, and other prominent protocols are examples of these layers. These protocols are in charge of network services such as file transfers, emails, client-server procedures, and web browsing, among others. There are no software applications in this tier. When a browser (software application) receives a request from a user to get a remote HTML document, the browser attempts to access the application layer to complete the request. The user's request or the data is subsequently passed on to the next layer for further processing.
Presentation Layer-6
In the seven-layer OSI model of computer networking, the presentation layer is layer 6 and serves as the data translator for the network. It is sometimes called the syntax layer. ~Wikipedia
The Presentation layer translates, compresses, and encrypts data received from the application layer before passing it down to the protocol stack in the case of an outgoing message. In the event of an incoming message, the Presentation layer decrypts and decompresses the data received from the Session layer before presenting it to the Application layer in an appropriate format. To facilitate readability across networks, data is translated (EBCDIC to ASCII) into a common format. For quick data transport, compression (Lossy/Lossless) is used, and encryption (SSL/TLS) is used to assure data security.
Session Layer-5
The session layer provides the mechanism for opening, closing and managing a session between end-user application processes, i.e., a semi-permanent dialogue. ~Wikipedia
This layer's major role is to use authentication and authorization mechanisms to establish, maintain, and terminate sessions between client and server applications. After the authentication process is complete, a session is created. Only after the authorization process has been completed is a resource shared. The session layer keeps track of which data packets belong to which files and where the data packets received go. In this layer, data is exchanged in three different modes: simplex, half-duplex, and full-duplex.
Transport Layer-4
In computer networking, the transport layer is a conceptual division of methods in the layered architecture of protocols in the network stack in the Internet protocol suite and the OSI model. ~Wikipedia
The heart of the OSI model, this layer is responsible for end-to-end communication between devices, providing acknowledgement of successful data transmission or retransmission in the event of failure, and adding source and destination port numbers to the message header. Ports are virtual locations within an operating system that identifies a specific process or a type of network service and also where network connections start and end. The transport layer serves as a liaison between the hardware (service preparation) and software levels (deliver the services).
Let's have a look at some of the crucial functions that this layer performs.
- Segmentation
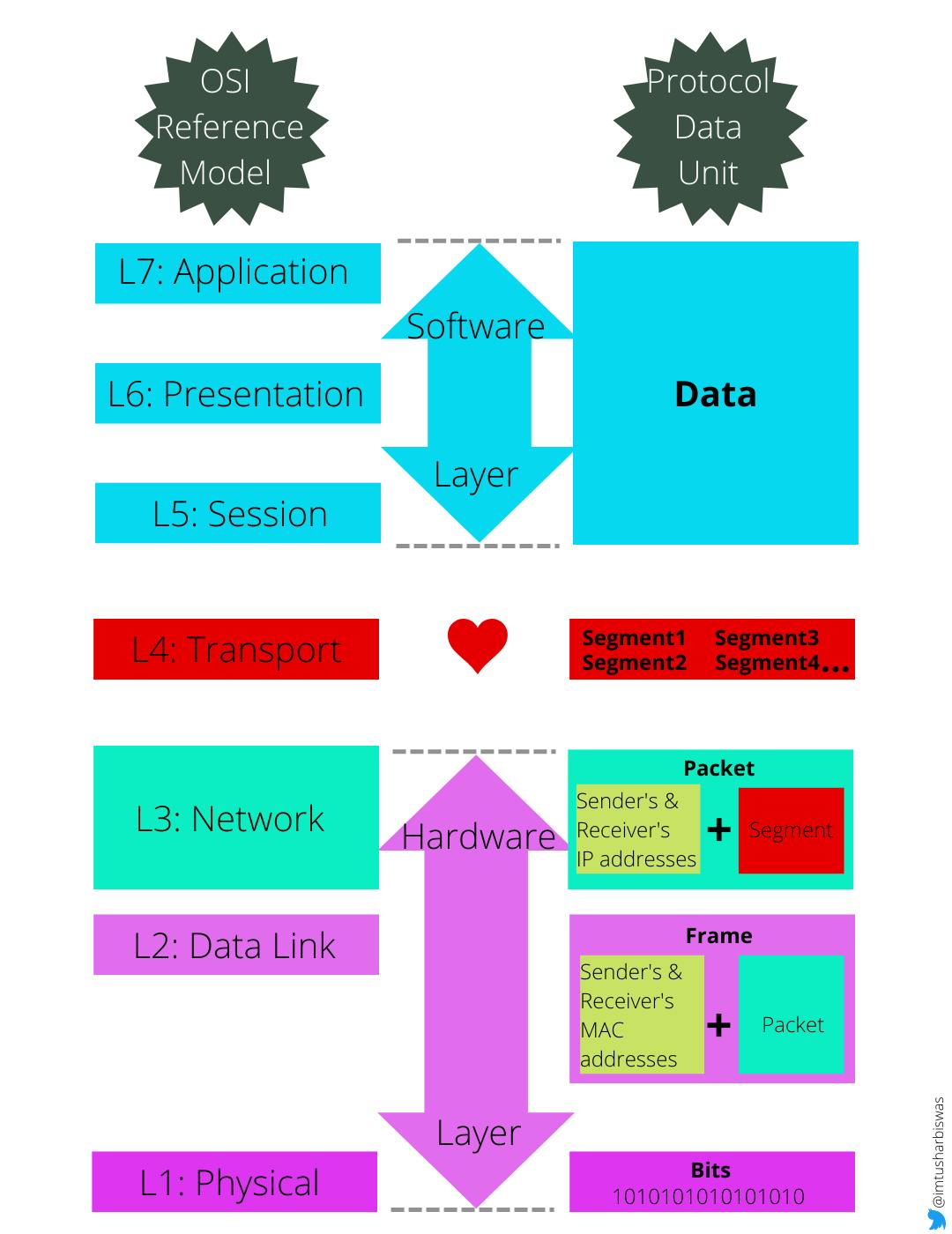
The software layer receives data and divides it into smaller units for transmission over the network. At this stratum, these smaller units are referred to as "Segments." During the transmission process, little segments (data units) are easier to manage than large and continuous streams of data. As a result, if portions of the segments are missing or corrupt at the receiving end, just those segments must be retransmitted, not the complete data. At the destination, the Transport layer reassembles the segments in order and delivers them up to the protocol stack.
- Port to Port / Process to Process data delivery
The Transport layer assigns source and destination port numbers (16 bit addresses) to segments in order to transport them to the correct destination. Software programs can be identified using port numbers. Process to process delivery is another name for this form of segment (data) distribution. Because software programs are a collection of processes in the end.
- End-to-end Connection establishment
User Datagram Protocol (faster, connection-less) and Transmission Control Protocol (slower, state & connection-oriented, acknowledgement based) are primarily used to establish end-to-end connections between source and destination. TCP is used in email, FTP, and the world wide web to prevent data loss, errors, and other problems. UDP, on the other hand, is used in applications such as VoIP, real-time multiplayer games, streaming media, and so on, where some loss of data, reordering, and errors are expected but not fatal.
- Multiplexing and Demultiplexing
Multiplexing refers to the process of assembling segments, which are actually streams of data received from different software programs at the same time, with the essential information, and delivering them to the network layer. Demultiplexing is the process of delivering received segments to the correct socket (port number + IP address) upon reception.
- Data-Flow control
After establishing a connection to hold incoming data, both the sender and receiver receive a buffer, which they share. The receiver sends a window advertisement as soon as the communication begins (amount of free buffer space). A positive window (with free buffer space) or a zero window (with no buffer space) can be advertised. The sender will continue to deliver data based on the buffer space available at the receiving end, and if the sender receives a zero window advertisement, the transmission will be terminated. TCP employs this mechanism to control data flow.
- Error Control
At the destination's Transport layer, a checksum (a collection of bits) is applied to each segment to identify corrupted segments. Automatic Repeat Request is used to retransmit a segment that has been lost or corrupted.
- Congestion control
Buffer overflow happens when too many senders in a network attempt to transfer data at a high rate, resulting in data loss. The network becomes even more crowded when the lost data is retransmitted. TCP uses algorithms and methods such as network congestion-avoidance, which comprises various components of an Additive Increase/ Multiplicative Decrease scheme,slow start, and congestion window, among others, to handle this problem.
Network Layer-3
The network layer is responsible for packet forwarding including routing through intermediate routers. ~Wikipedia
The sender and receiver's IP addresses are added to the segment received from the Transport layer in this tier, and the modified data units are referred to as packets. The network layer uses mechanisms such as logical addressing (assigning IP addresses), routing, and path determination to send and receive packets from one network to another. The sender and recipient can communicate with each other in a variety of ways. Protocols (OSPF, BGP, IS-IS) are used by L3 devices to establish the best potential path for data delivery.
Data link Layer-2
This layer is the protocol layer that transfers data between nodes on a network segment across the physical layer. ~Wikipedia
The Data Link layer receives data packets from the network layer with the sender and receiver's IP addresses and adds the sender and receiver's MAC addresses (a unique identifier embedded in the NIC by the manufacturer) to build a frame (data unit) and pass it on to the next layer.
Physical Layer-1
The layer most closely associated with the physical connection between devices. ~Wikipedia
Finally, depending on the type of medium being used by the Physical layer, the bits (0,1) are transformed to various types of signals (electrical, radio, or optical) and communicated over actual communication channels (LAN cable, fiber optics, wi-fi etc.) This layer is in charge of sending and receiving unstructured crude data between devices across a physical link.
6. Protocol Data Unit (Bonus Topic)
In telecommunications, a protocol data unit is a single unit of information transmitted among peer entities of a computer network. It is composed of protocol-specific control information and user data. ~Wikipedia
With the help of the diagram below, we can see how each layer treats a piece of data.
Alright friends, we just witnessed how data actually travels from source to destination using the OSI reference model, and perhaps this information will help us learn TCP/IP in the future as planned. And for those who are wondering why spend time on ancient things like these when blockchain, web3, crypto, and other hot topics are the talk of the town, I'd tell them that come what may, I'll cover all the tech-topics and everything will make sense in due time, so don't worry... "KENNO" 🐛😎 is my name!
Hello there 👋 Thank you very much for taking the time to read this post🙏 Please feel free to share your ideas, recommendations, comments, questions and I'll forward them to "Kenno". Also, if you've written something or have a reference on the same subject, kindly share it with me and I'll do my best to read it. I'll catch up with you later🙂